Are you confident that your hardware security is robust enough to catch critical security flaws early in your design process? Incorporating a ‘shift-left’ approach —integrating security from the early stages of the development cycle—can greatly enhance your cybersecurity defenses. This is crucial for semiconductor devices, whose security vulnerabilities become orders of magnitude more expensive to address post-production.
Increasing design complexity makes uncovering security threats pre-silicon even more challenging. It’s a task that requires tightly coordinated efforts among product development, functional testing, and security testing teams. At a high level, the goal is to move security awareness and detection of the weaknesses that lead to vulnerabilities earlier in the design process—to shift security considerations left on the product development timeline. At a more granular level, there are a number of elements to consider.
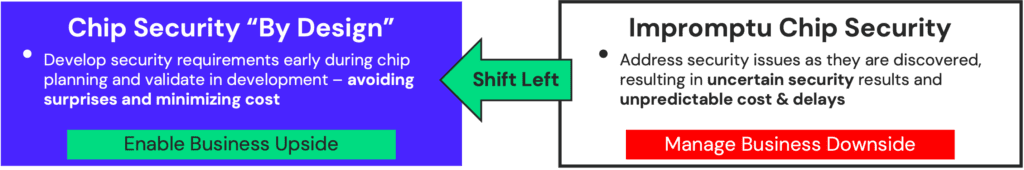
Implementing the Shift Left
Here’s a series of best practices to embed the principles of ‘shift-left’ security into the lifecycle of your chip design planning and execution.
- Integrated Security Early in the Design Phase:
Actionable Steps:- Formulate and Document Basic Security Design Requirements:
- Begin by defining foundational security requirements based on the primary functions and critical assets of the hardware. Hardware assets should be categorized into their potential threats as they relate to the CIA triad- Confidentiality, Integrity, and Availability.
- Align stakeholders on the security requirements and then document them following industry standards and best practices, creating a solid foundation for security measures.
- Implement and Verify Core Security Features:
- During the design phase, incorporate hardware-specific security features like tamper detection, secure boot, and cryptographic modules.
- Apply foundational verification to confirm that these security features perform as expected, ensuring that the implementation is secure and effective from the outset.
- Enhanced Component-Level Security:
Actionable Steps:- Analyze and secure each hardware component independently.
- Further test these components for correct behavior at the edges where they interact with other components.
- Firmware Security Measures:
Actionable Steps:- Develop and enforce strict security protocols for firmware development, including code signing and secure update processes.
- Regularly update firmware to address new vulnerabilities, ensuring compatibility with hardware security features.
- Supply Chain Security Management:
Actionable Steps:- Implement stringent security checks, audits, and signoff for third-party components.
- Establish secure communication protocols with suppliers to ensure the integrity of hardware components.
- Continuous Security Training for Hardware Teams:
Actionable Steps:- Provide hardware engineers with specialized training on emerging security threats and mitigation techniques.
- Encourage a culture of security awareness and responsibility among hardware development and verification teams.
By focusing on these specific and actionable best practices, organizations can significantly strengthen their hardware security posture, aligning with the principles of shift-left security. This approach mitigates risks and fosters a proactive security culture throughout the hardware development lifecycle.
Radix: Your Co-pilot in the Shift Left
Radix accelerates the detection of weaknesses early in the chip design lifecycle with in-depth analysis and insight into unexpected behaviors, enabling you to bolster security protections effectively. Radix helps define verifiable security requirements based on the underlying asset you are trying to protect and integrates with existing verification environments to extend security verification from IP blocks to full system-on-chip implementations. This approach is particularly beneficial in detecting and mitigating vulnerabilities arising from operating environment changes or firmware and software integration, ensuring end-to-end, measurable security.
Radix is a valuable resource for implementing early-stage “shift-left” strategies. We’re always happy to provide more detail — contact us for a demo…
