Traditional security tools are no longer enough.
Traditional verification methods ensure that security features work as intended. They’re well-suited for formal verification and directed tests and SVA, as they verify expected behavior.
Adding Radix to your existing verification environment gives you the strongest security coverage, with a repeatable process for validating security properties and the absence of unexpected security flaws across the design lifecycle—from block level to full SoC, including software.
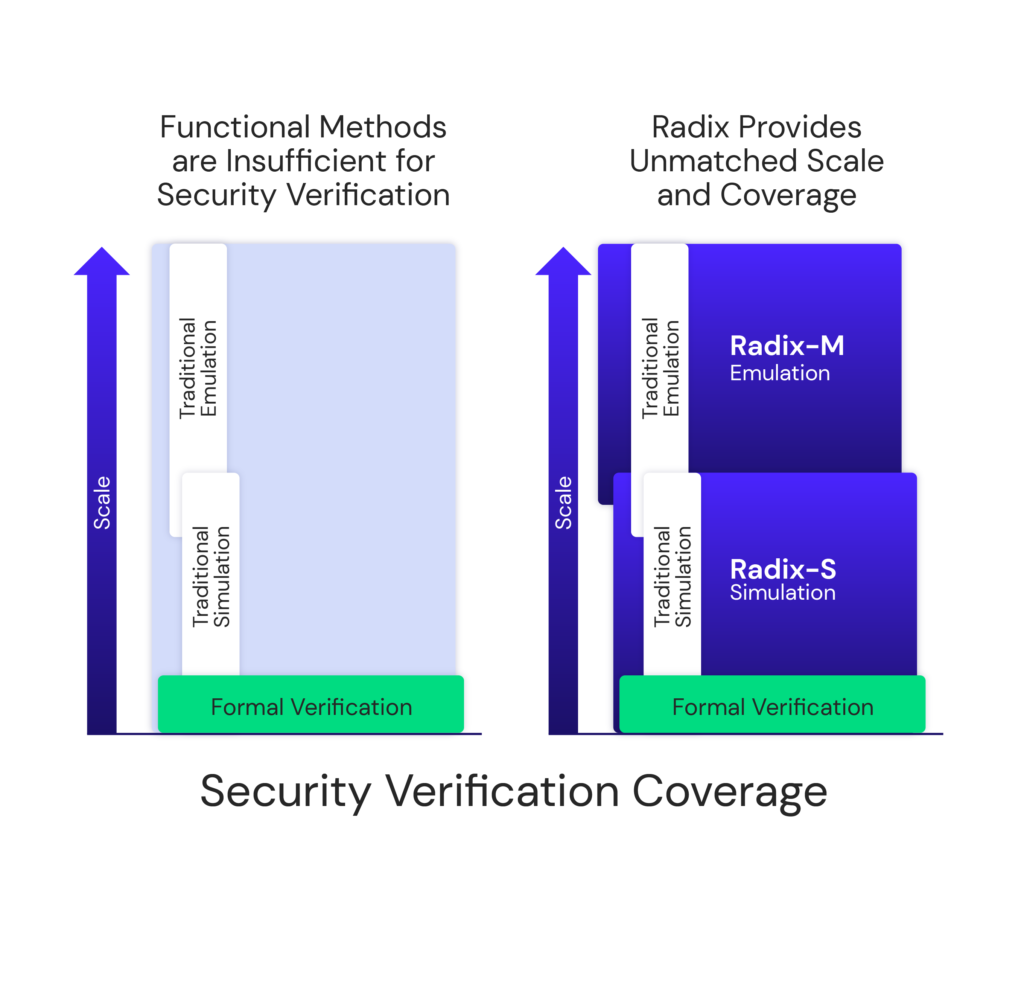
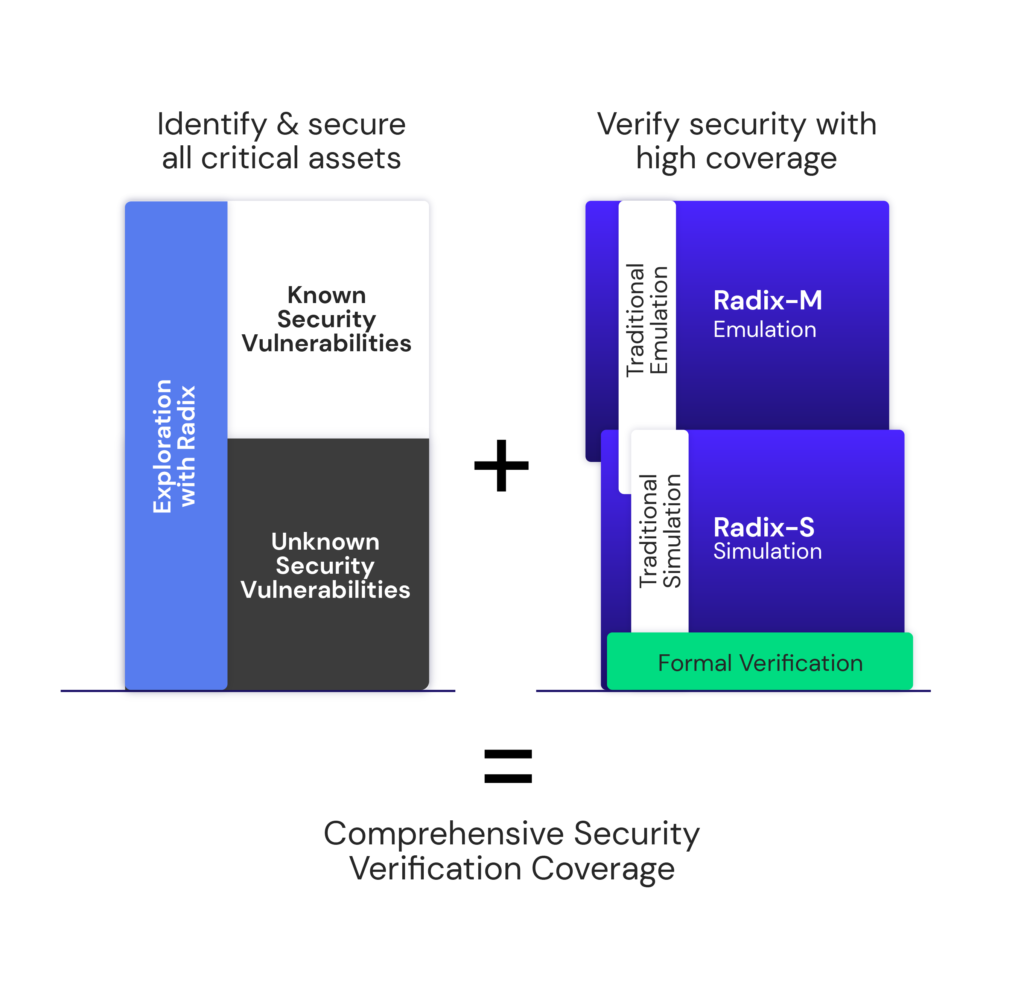
Uncover the broadest set of hardware vulnerabilities.
If you’re not verifying security at every stage of the semiconductor design life cycle, you could be missing critical weaknesses. Cycuity’s next-gen technology, Radix, lets you avoid late-stage surprises by systematically detecting known and yet-to-be-discovered security vulnerabilities—including those documented in best-practice standards like MITRE Common Weakness Enumeration (CWE)—ensuring they don’t end up in your final design.
Radix is next-generation hardware security verification.


How Radix is different.


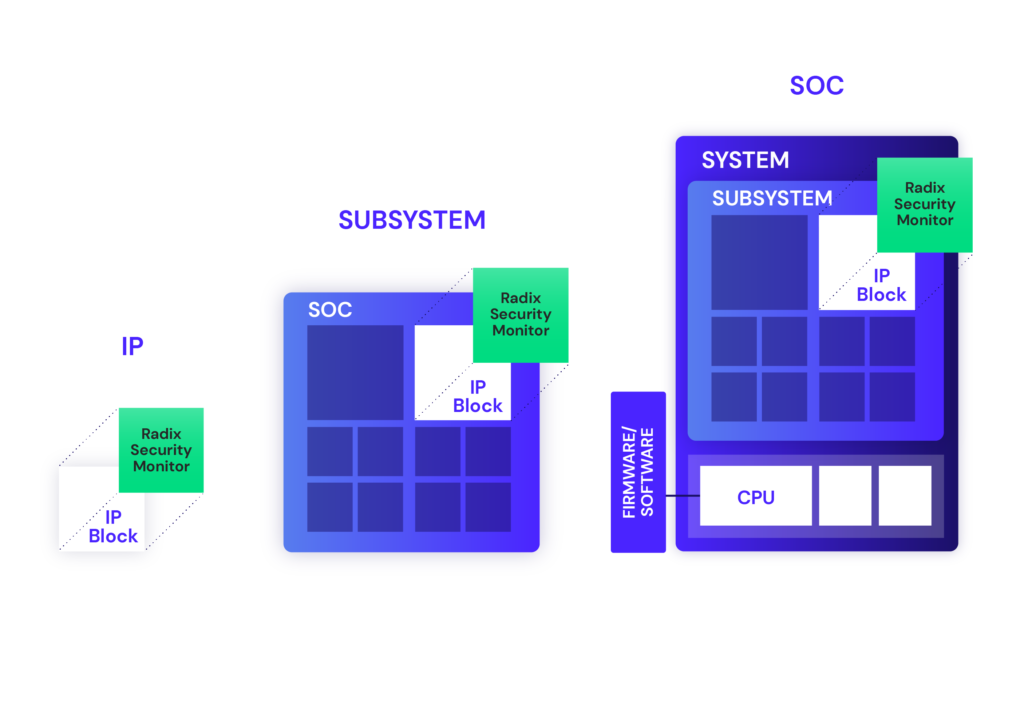
Asset-Based Methodology
Utilizing a uniquely comprehensive security verification methodology centered around security assets, Radix gives you broad, systematic security coverage of both known and previously unknown weaknesses.
Powerful Security Rules
Ultra-compact and straightforward to write, Radix security rules are validated in any existing verification environment. Not only do they enable you to automate rigorous security verification throughout development, they can be reused across the design cycle, and even across multiple design projects.
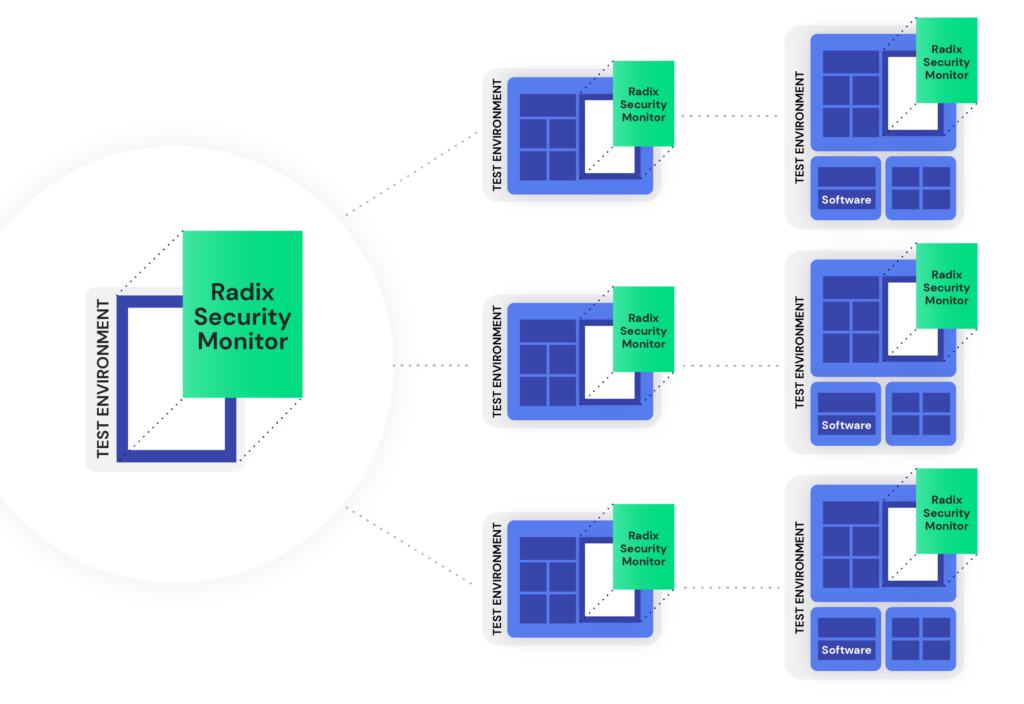

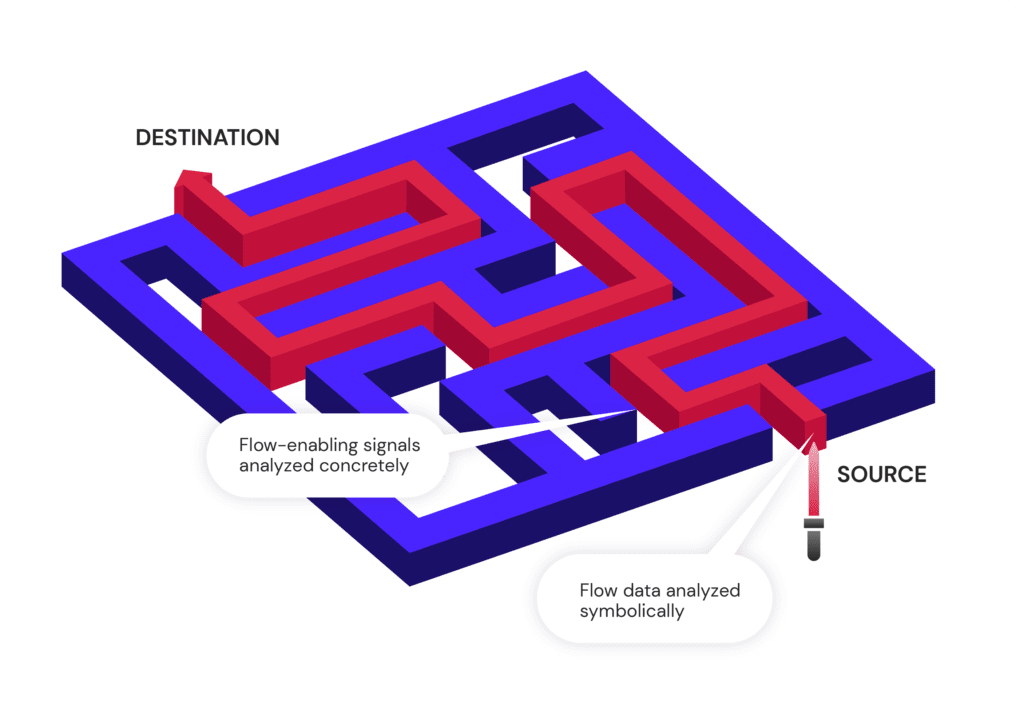

Automated Asset Tracking
Radix’s patented information flow analysis tracks and traces all security assets independently of their values, as they flow across the chip and through logical and sequential transformations. Offering unique insights into the design’s security behavior, Radix gives you a foundation for powerful security discovery and verification.
Security Assurance from Block to Firmware & Software
Radix combines the power of symbolic analysis with the scalability of simulation/emulation to give you the broadest security assurance by addressing the limitations of functional methods such as formal verification and SVA and UVM based simulation.

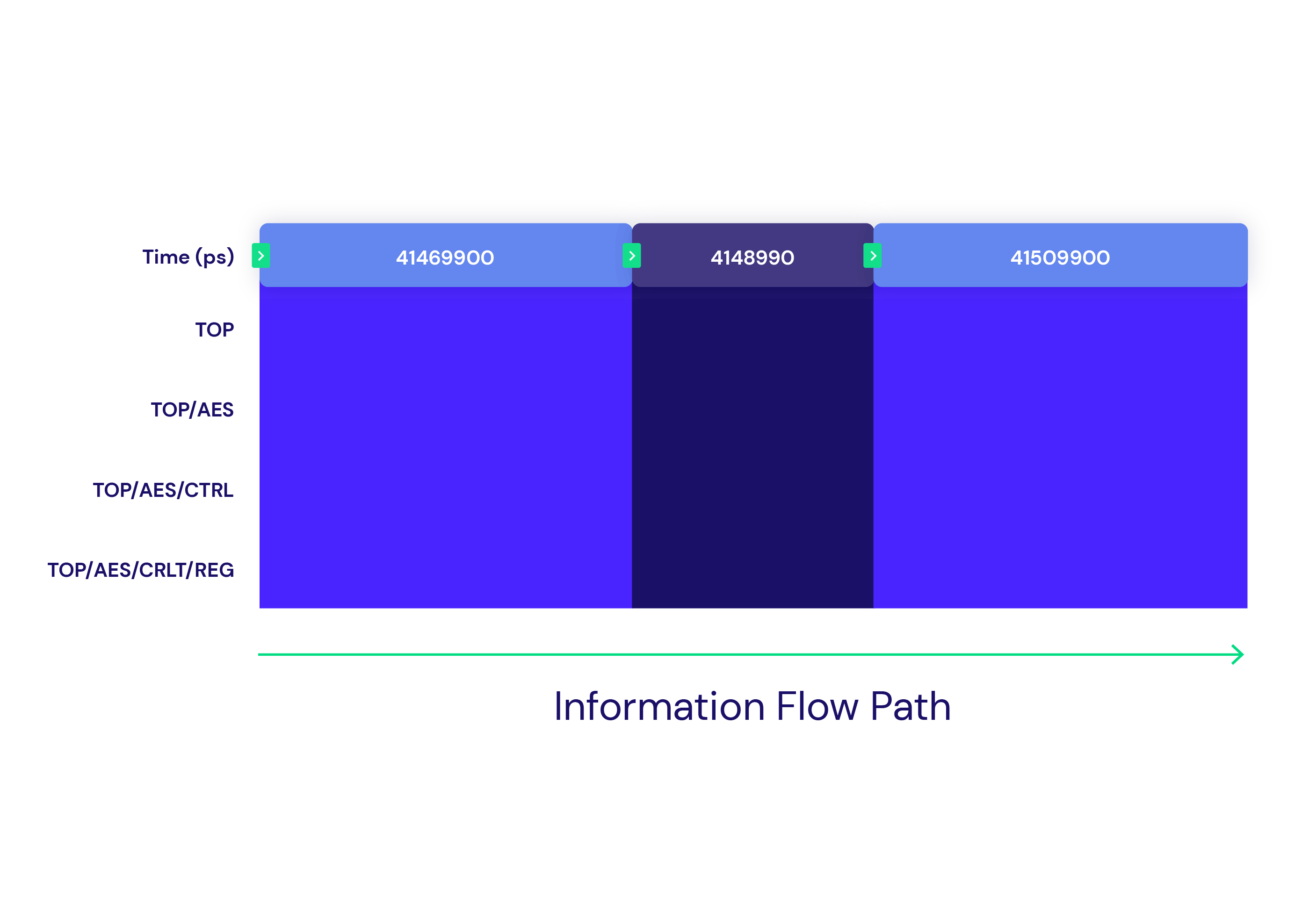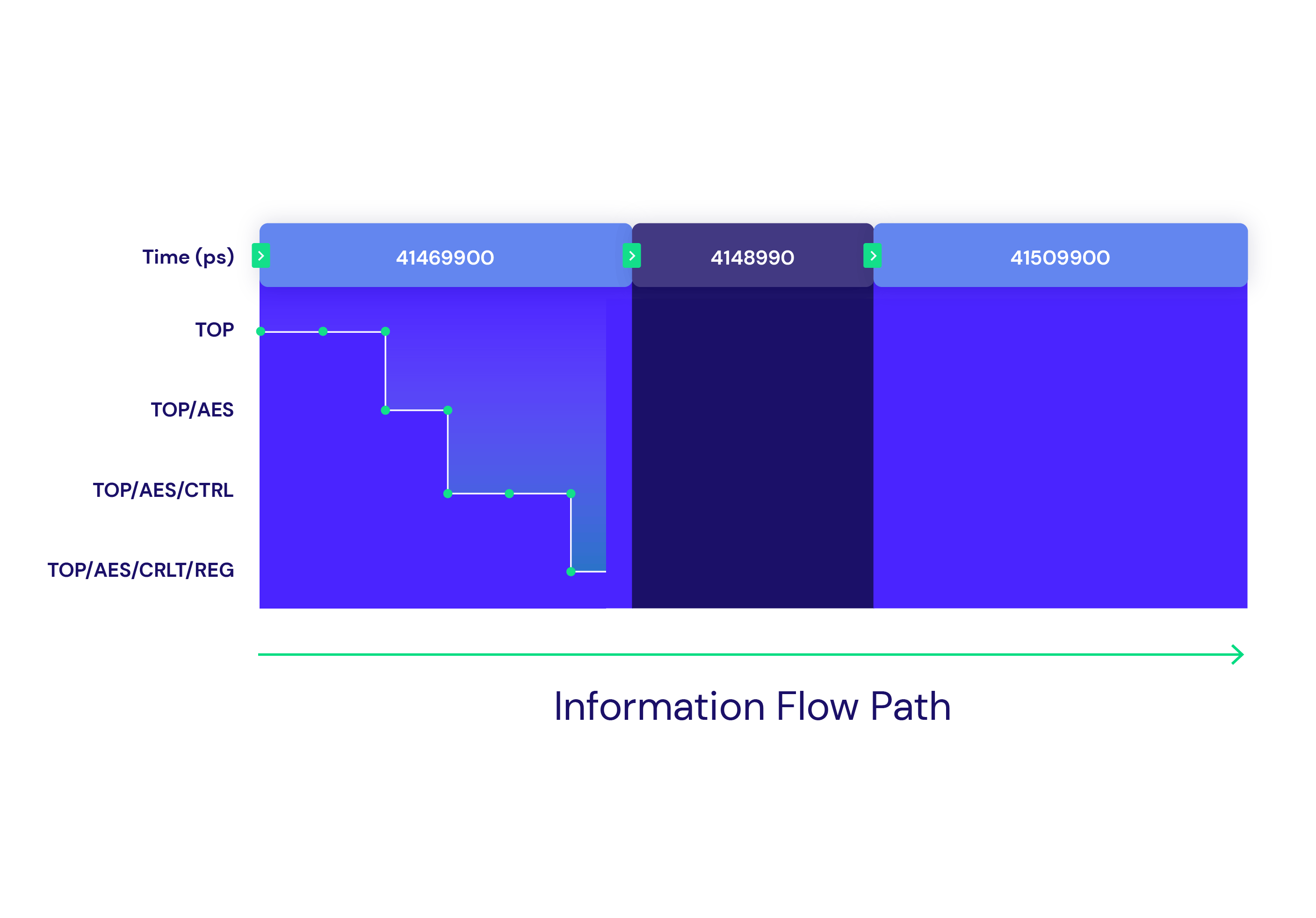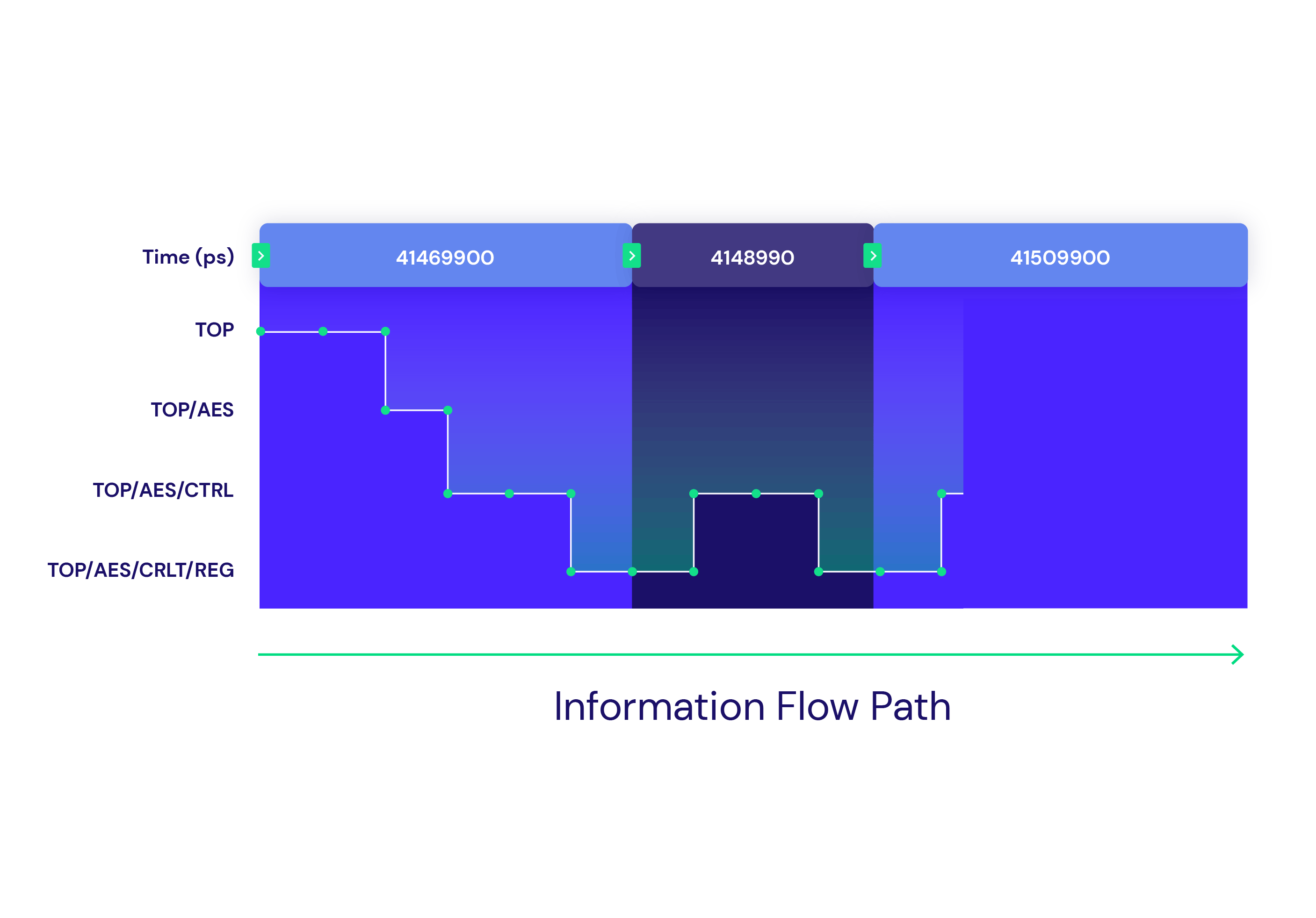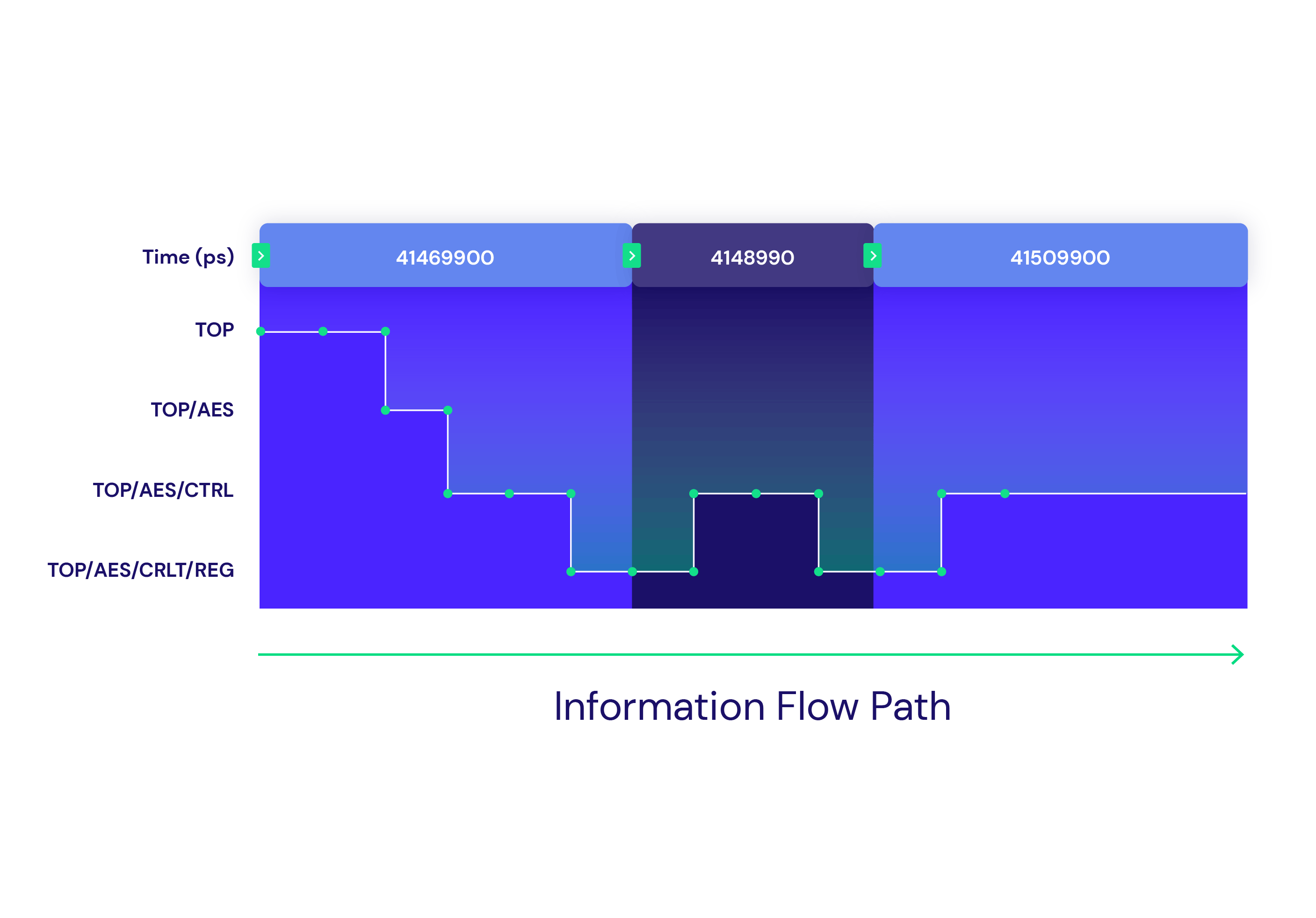

Real-Time Analysis Capabilities
Radix provides real-time analysis capabilities that highlight the flow of security assets to understand a design’s security behavior, and identify the root cause of uncovered vulnerabilities. Multiple views give you insight into flow hierarchy, data, and control values, as well as special features for inspecting memories.
Use Cases
As the complexity of chip design grows, so do threats that can undermine customer trust—and your bottom line. See how Cycuity can give your business end-to-end hardware security throughout the product life cycle.
Roots of Trust
Hardware roots of trust have become the foundation of semiconductor security. See how you can build a more secure system with hardware security assurance from Cycuity.
Application Processors
Modern microprocessors are core to the applications that power cars, data centers, and mobile phones. As their performance has grown, so have their vulnerabilities.
System-On-Chips
Fundamental to the security of IoT, automotive, and datacenters is the security of the SoCs that power them. Verify the security of increasingly complex SoCs with Radix.
Microcontrollers
Microcontrollers are responsible for the core functionality of embedded devices in consumer electronics, cars, medical devices and more. Securing their operation is critical for product safety and security.


Automotive Cybersecurity
Modern vehicles depend on an array of electronics, sensors, and computer systems. Confidently maintain your security posture against these expanding attack surfaces with Radix.


CWE
The industry’s formal list of common hardware weaknesses is the Common Weakness Enumeration, a list created and curated by MITRE. For organizations seeking a “secure by design” approach, testing against the CWE list is critical.
Mercury is proud to continue our important collaboration with Cycuity, leveraging their Radix security verification technology to deliver the most secure custom integrated circuits to our customers.
Shaun McQuaid
Senior Director of Product Management, Processing Division, Mercury Systems


Level up your hardware security today.
Get the confidence of end-to-end hardware security assurance throughout the product lifecycle. Contact us today to see how.
