Many of today’s systems are built around specialized computing hardware that includes intellectual property (IP) to accelerate algorithms used in applications such as Machine Learning and Artificial Intelligence, or Cryptography. While a specific algorithm or system may be secure in theory, a final System on Chip (SoC) implementation may not be as secure due to the integration of that IP with multicore processors, memory, standard interfaces, and a software stack.
SoC teams have used functional verification solutions such as simulation and emulation for years to verify the functionality of designs, pre-silicon. These solutions, while necessary for functional correctness, unfortunately lack the capability to track the flow of information throughout the design, leading to a lack of insight that is required for system security.
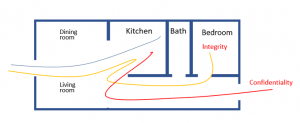
So, what is information flow? Let’s use an analogy of a house. The house has a front door that leads to a living room and beyond that a kitchen, with a hallway connecting a bathroom, bedroom and backdoor. Over the years of experience living in houses, we would expect that if I came through the door with groceries, that I would take them to the kitchen. This would be the expected flow. However, if I entered and took them through the kitchen directly to the bedroom, then out the back door, this would be abnormal behavior.
Leveraging information flow for security, we look for security based on the confidentiality and integrity of design assets such as configuration settings, parameters and weights for machine learning algorithms, or cryptographic keys. Continuing with the analogy, because the groceries (encryption key) went from the kitchen (crypto IP) to the bedroom (memory) the expected flow has been violated.
Next, if someone snuck into the kitchen through the back door (standard interfaces) and took our groceries (encryption key), then the confidentiality and integrity of the kitchen has been violated.
Existing simulation/emulation-based functional verification tools do not track information flow through the design. Labor-intensive negative tests must be developed to check security-specific corner cases for the highest priority threats, but without the ability to track information flow in the design, negative testing is extremely limited.
For example, writing a directed SystemVerilog test or assertion to verify the confidentiality of an encryption key is extremely time-consuming and difficult to compose. Traditional verification infrastructure can find an expected ciphertext value; however, other transformations that correspond to leakage of intermediate states are difficult to enumerate and check for using directed tests and assertions. A key could go through an infinite number of simple transformations over time (for example, exclusive-or with plaintext, bit shift, etc.) from which an attacker who can observe these transformed key values can recover the original key. More complex indirect leakages, through timing side-channels for example, may be impossible to detect. Similar difficulties are encountered when attempting to verify integrity of assets using traditional verification infrastructure.
Code reviews and penetration testing both involve reasoning about information flow, however, because these are manual processes, they require an enormous amount of effort. This effort does not scale well as design size and complexity increases.
Information flow analysis as implemented in Tortuga Logic’s Radix-S and Radix-M tools complements and leverages functional verification. It lets you track information over time. It also helps determine what path the information took to get through the design regardless of transformations to the values carrying that information. Information flow can also provide insight into a device’s unintended behavior by allowing visualization of the information paths within a design.
With information flow analysis, even if the information is transformed, security and verification teams can ensure that trusted data is not leaked unintentionally and that internal data is not manipulated through unintended channels. For more information on Information Flow Analysis, contact us at info@tortugalogic.com.
