Scalable, Measurable Hardware Security Verification
Prevent hardware vulnerabilities and make
data-driven decisions with pre-silicon security assurance.
How Radix Is Different
Radix brings a more systematic and robust approach to hardware security verification. Explore
and visualize how information flows through your chip, create intuitive and measurable security requirements, and monitor their effectiveness. You’ll discover vulnerabilities sooner and make
sign-off decisions based on data instead of guesswork.

Make Secure Assets Your Strategic Foundation
Radix starts with the sensitive assets you need to protect, and builds a comprehensive security verification methodology around them that is systematic, comprehensive and measurable. By defining security requirements based on specific assets, you can more effectively mitigate weaknesses and enhance the overall security posture of you chip.
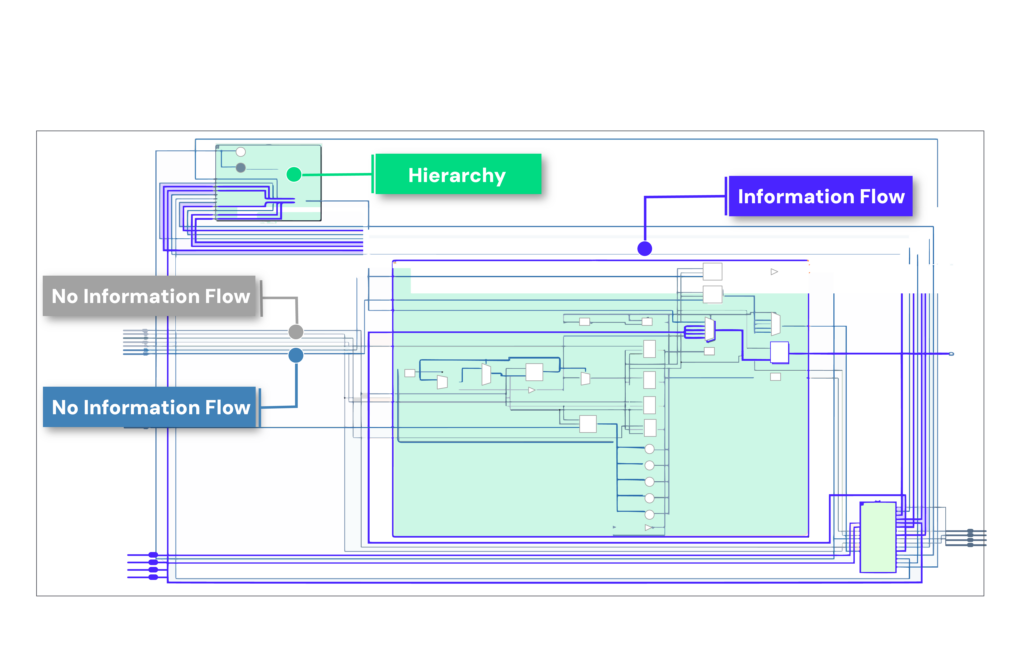
Explore Security with Depth and Precision
Radix goes beyond the typical “pass or fail” checks, offering unmatched design exploration and security analysis capabilities. Visualize your design assets using information flow overlay, schematic, or waveform views to understand the behavior of security functions and quickly identify the root cause of security weaknesses.
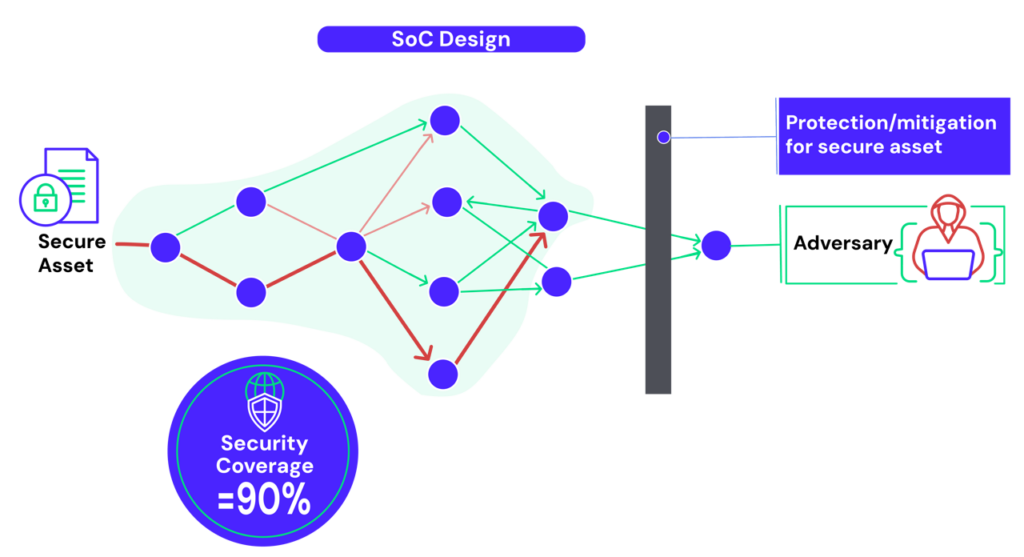
Measure Your Security Coverage
Radix calculates a security coverage metric tailored for hardware designs, empowering you to precisely measure the effectiveness of your security protocols. By pinpointing areas needing further testing, Radix ensures your chip’s design security is comprehensive and robust.
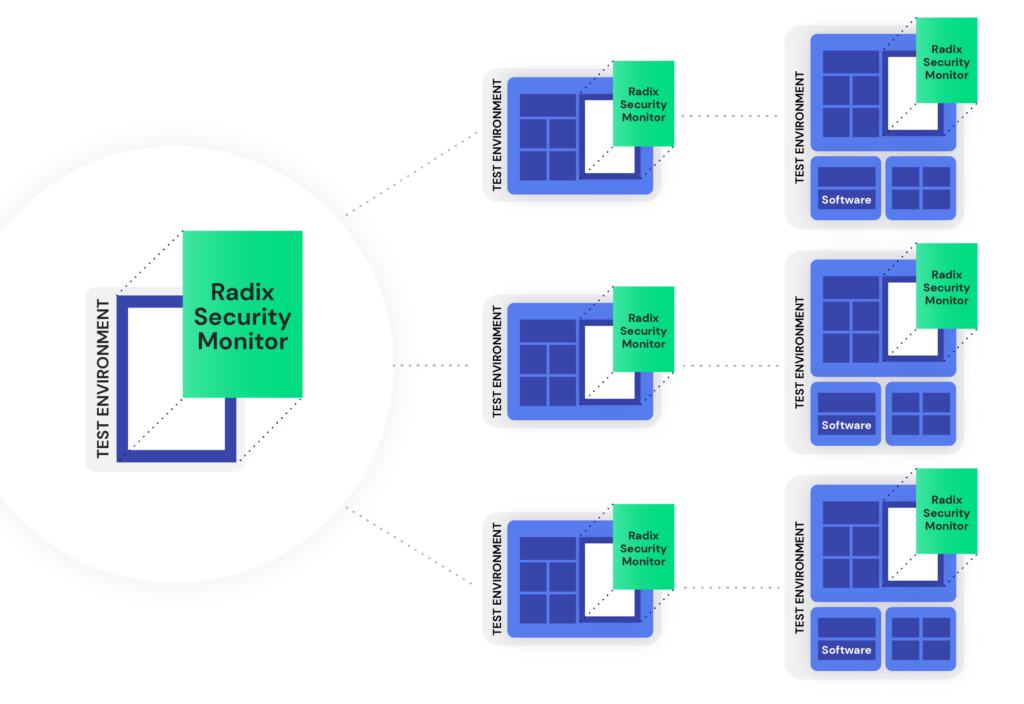
Create, Monitor and Verify Security Rules Efficiently
Radix seamlessly converts your security requirements into rules that can be applied and efficiently managed for systematic security verification throughout the development process. Concise and straightforward to write, Radix security rules offer wider security coverage, and can be reused across multiple design projects. Once created, Radix rules are automatically converted into a security monitor incorporated into the design and run in standard simulators and emulators.
Use Cases
As the complexity of chip design grows, so do threats that can undermine customer trust—and your bottom line. See how Cycuity can give your business end-to-end hardware security throughout the product life cycle.
Roots of Trust
Hardware roots of trust have become the foundation of semiconductor security. See how you can build a more secure system with hardware security assurance from Cycuity.
Application Processors
Modern microprocessors are core to the applications that power cars, data centers, and mobile phones. As their performance has grown, so have their vulnerabilities.
System-On-Chips
Fundamental to the security of IoT, automotive, and datacenters is the security of the SoCs that power them. Verify the security of increasingly complex SoCs with Radix.
Microcontrollers
Microcontrollers are responsible for the core functionality of embedded devices in consumer electronics, cars, medical devices and more. Securing their operation is critical for product safety and security.
Cybersecurity Compliance
As regulations evolve to keep pace with innovation, ensure that your hardware not only complies with existing frameworks but is also resilient against future hardware security challenges.
Incorporating CWE
The industry’s formal list of common hardware weaknesses is the Common Weakness Enumeration (CWE), a list created and curated by MITRE. For organizations seeking a “secure by design” approach, testing against the CWE list is critical.
See How Radix Can Improve Your Security
Hardware security is a journey. Where are you in the maturity of your hardware security?
